Understanding the Proxy Pattern
Table of Contents
- Introduction
- What is the Proxy Pattern?
- Types of Proxy Patterns
- Real-World Applications
- Implementing the Proxy Pattern in Java
- Advantages of the Proxy Pattern
- Disadvantages of the Proxy Pattern
- Best Practices
- Conclusion
Introduction
In software design, managing access to objects efficiently is a crucial challenge. The Proxy Pattern, a structural design pattern, provides a way to control access to objects, add security layers, implement lazy initialization, and even optimize performance through caching.
This blog explores the Proxy Pattern, its types, real-world use cases, implementation, advantages, and best practices.
What is the Proxy Pattern?
The Proxy Pattern provides a substitute or placeholder for another object to control its access. Instead of directly interacting with the real object, clients communicate with a proxy that manages, controls, or enhances the behavior of the real object.
Key Concepts of the Proxy Pattern
- Real Object (Real Subject): The actual object that performs the intended operations.
- Proxy Object (Proxy): A stand-in for the real object, which controls access, manages resources, or provides additional functionalities.
- Client: The entity that requests services from the real object via the proxy.
Types of Proxy Patterns
There are different types of proxies, each serving a unique purpose.
1. Virtual Proxy
Used for lazy initialization to improve performance. The real object is created only when it is required.
Example:
- Loading high-resolution images only when they are displayed.
- Deferring object creation in memory-intensive applications.
2. Protection Proxy
Controls access permissions to an object.
Example:
- Role-based access control in software applications.
- Restricting access to sensitive data based on user authentication.
3. Remote Proxy
Acts as a local representation of an object that exists in another location, often used in distributed systems.
Example:
- Remote Procedure Calls (RPC).
- Accessing a database on a remote server.
4. Cache Proxy
Stores frequently used results to optimize performance.
Example:
- Web caching (CDN services).
- Database query caching to avoid redundant processing.
5. Smart Proxy
Adds extra functionality before or after accessing the real object, such as logging, reference counting, or resource tracking.
Example:
- Logging API calls.
- Managing database connections efficiently.
Real-World Applications
The Proxy Pattern is widely used in various domains, including:
- Web Development: Caching proxies for faster content delivery.
- Security Systems: Protection proxies for access control.
- Distributed Systems: Remote proxies for seamless communication between systems.
- Resource Management: Virtual proxies for efficient memory usage.
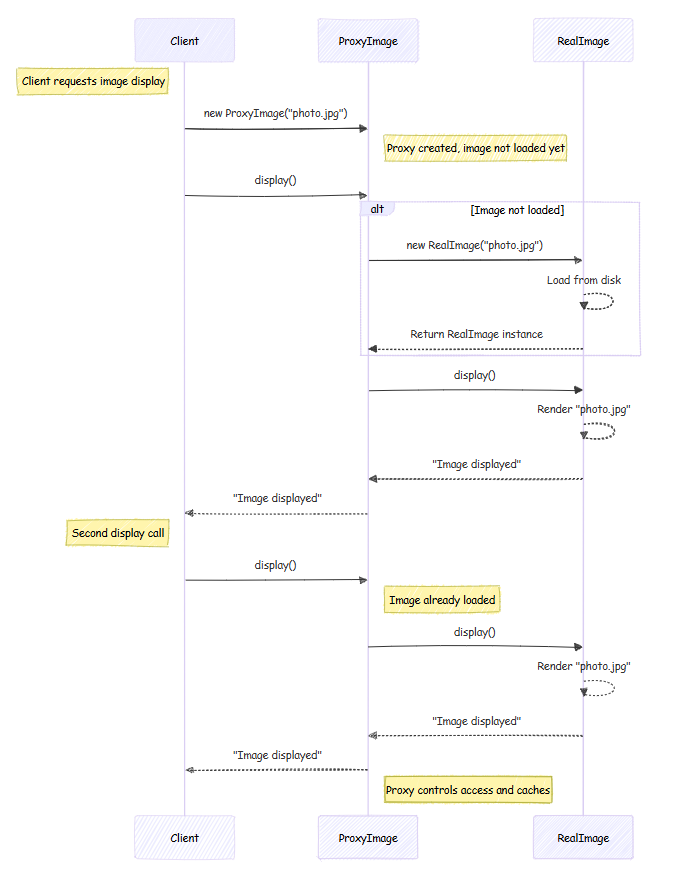
Implementing the Proxy Pattern in Java
Let’s walk through a step-by-step implementation of the Proxy Pattern in Java.
Step 1: Define the Interface
public interface Image {
void display();
}
Step 2: Create the Real Object
public class RealImage implements Image {
private String filename;
public RealImage(String filename) {
this.filename = filename;
loadFromDisk();
}
private void loadFromDisk() {
System.out.println("Loading image: " + filename);
}
@Override
public void display() {
System.out.println("Displaying image: " + filename);
}
}
Step 3: Implement the Proxy Class
public class ProxyImage implements Image {
private RealImage realImage;
private String filename;
public ProxyImage(String filename) {
this.filename = filename;
}
@Override
public void display() {
if (realImage == null) {
realImage = new RealImage(filename); // Lazy initialization
}
realImage.display();
}
}
Step 4: Client Code Using the Proxy
public class Client {
public static void main(String[] args) {
Image image = new ProxyImage("test_image.jpg");
// Image will be loaded only when display() is called
image.display();
}
}
Output
Loading image: test_image.jpg
Displaying image: test_image.jpg
Advantages of the Proxy Pattern
- Controlled Access: Proxies can restrict or manage access to the real object.
- Lazy Initialization: Improves performance by deferring object creation.
- Enhanced Functionality: Proxies can add additional behaviors like logging or caching.
- Security: Protection proxies can enforce access control.
Disadvantages of the Proxy Pattern
- Increased Complexity: Introduces additional layers, making the system harder to understand.
- Performance Overhead: Proxies may introduce slight delays due to extra processing.
- Overuse: Using proxies unnecessarily can lead to bloated code.
Best Practices
- Use Proxies Sparingly: Only use proxies when necessary to avoid unnecessary complexity.
- Combine with Other Patterns: Proxies work well with patterns like Decorator or Factory.
- Optimize for Performance: Ensure that the proxy does not become a bottleneck.
- Document Clearly: Clearly document the purpose of the proxy to avoid confusion.
Conclusion
The Proxy Pattern is a powerful tool for controlling access to objects, optimizing performance, and adding security layers. By understanding its types, advantages, and best practices, you can effectively implement it in your projects to create more efficient and secure systems.
Whether you're working on web development, distributed systems, or resource management, the Proxy Pattern can help you achieve your goals with elegance and efficiency.